Important Update: Community URLs redirect issues are partially resolved. Learn More. .
- Archer Community
- News, Events & Groups
- Archer Blogs
- You Just Started a New Job!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In my last blog "Translating Security Leadership into Board Value" I introduced RSA's most recent Security for Business Innovation Council report along with the concept of Business Driven Security. A business driven security strategy is of great value to existing CISOs, information security leaders and the organizations they serve.
To explore business driven security concepts a little more, imagine that you have just accepted a job at a different company, to be responsible for the company’s entire information security program. You know very little about your new company except what you have read on their website, via Google searches, and from published financial statements. You are very excited to start your new job and you know your first priority is to complete a preliminary assessment of information security in a very short period time.
On day one, you know you don’t know:
- The information most important to the organization;
- The information security regulations imposed upon your organization;
- How much important information needs to be protected;
- Where the important information resides inside the organization and with third parties the organization does business with;
- What technical and organizational measures the organization has in place to manage and monitor information risk;
- Whether the technical and organizational measures that are in place are commensurate with the level of information security risk; and
- Whether technical and organizational measures are designed and sufficient to tell you the potential impact to the organization should the measure fail, a vulnerability arise, or breach occur.
By utilizing RSA Archer and consistently applying risk management principles such as those outlined in ISO 31000, you are able to build the foundational elements of a business driven security strategy for just about any type of information that is important to the organization whether it is intellectual property; imposed by contractual obligation, such as PCI; or imposed by regulations such as GLBA or EU-GDPR.
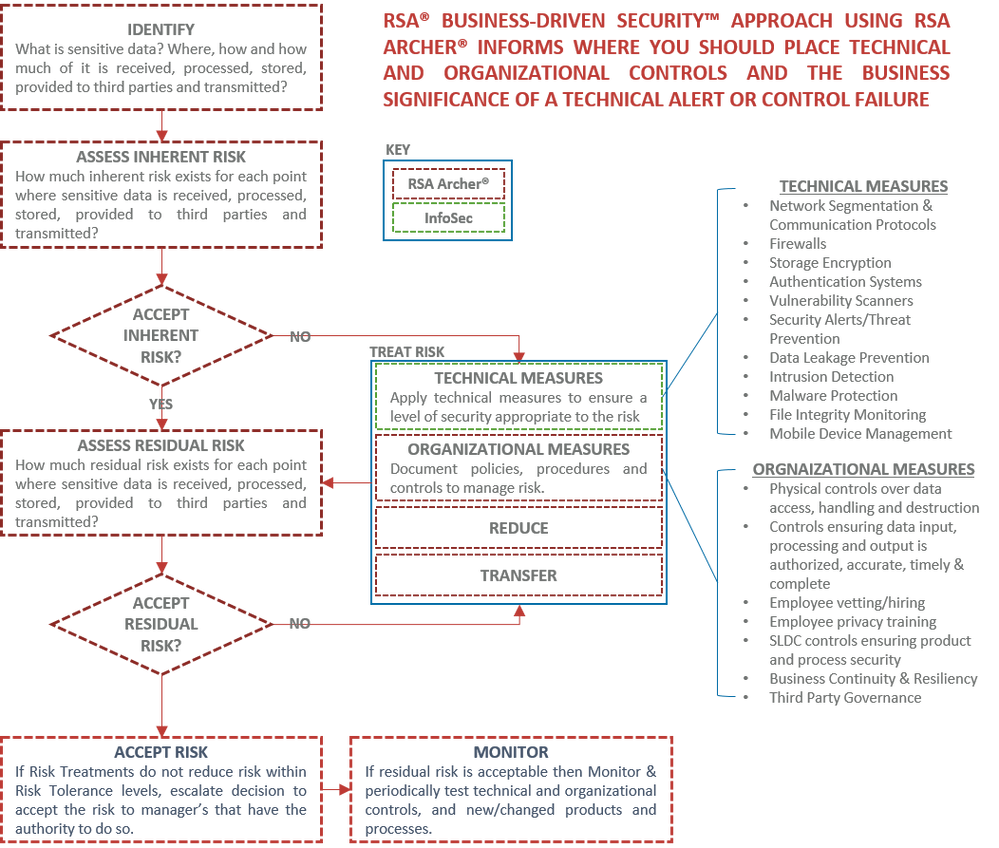
The following diagram provides a condensed view of where RSA Archer would be used to enable a business driven security strategy. RSA Archer is used to document the identification of information at risk, assess inherent and residual risk around the information, evaluate the acceptability of the risk; document the technical and organizational measures to mitigate risk; document decisions regarding the acceptance of risk; performing control tests; and to monitor the on-going risk profile, related key risk and control indicators, and outstanding risk issues to be remediated. Lastly, RSA archer is used to capture vulnerabilities, incidents, and control gaps, provide insight into their business context and the amount of associated risk so that problems are remediated based on their priority and significance.
By utilizing RSA Archer as your foundation for Business Driven Security you are able to answer the questions you set out to answer. You now know:
- What information is most important to the organization;
- What information security-related regulations are imposed upon the organization;
- How much important information needs to be protected;
- Where the important information resides inside the organization and with third parties
- What technical and organizational measures the organization has in place to manage and monitor information risk;
- Whether the technical and organizational measures in place are commensurate with the level of information security risk;
- Whether the risk treatment measures are designed and sufficient to tell you the potential impact to the organization should the measure fail or indicate that a vulnerability or breach has occurred; and
- Whether the information security risk profile is changing and why it is changing
All of this information informs your conversation with executive management and the board. You are able to articulate the amount of risk in business terms, justify security expenditures, and state how much various breaches might impact the organization, should they occur. Finally, with your documentation and methodical approach, you are able to demonstrate to all of your stakeholders, including regulators, that you have a sound, logical, and defensible risk-based approach to information security.
Learn more about how Archer can enable a business driven security strategy in your organization with this just released white paper: 7 Steps to Build a GRC Framework Aligning Business Risk Management for Business-Driven Security.
- Ent Credit Union Success utilizing Archer for Third Party Risk Management in Case Studies
- Cross-Reference fields DATA not visible unless record reopened in Archer Custom Objects Forum
- Data Feed Monitor Error in Archer API Users
- Listing users from a Record Permissions field with a Custom Object in Archer Custom Objects Forum
- Easily Test Archer APIs with the Archer API Testing Tool & Utility in Archer Blogs