Important Update: Community URLs redirect issues are partially resolved. Learn More. .
- Archer Community
- News, Events & Groups
- Archer Blogs
- The Synergy of Vendor and IT Risk Management Solutions
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
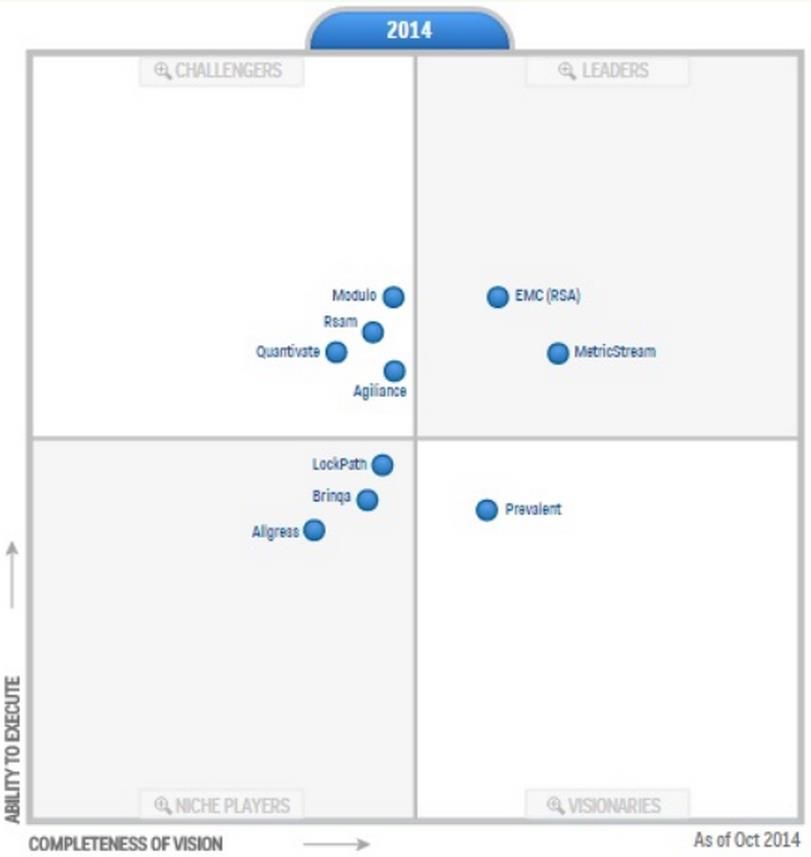
In October last year, Gartner released their Magic Quadrant for IT Vendor Risk Management, positioning EMC (RSA) in the Leader's Quadrant, with the highest ability to execute.
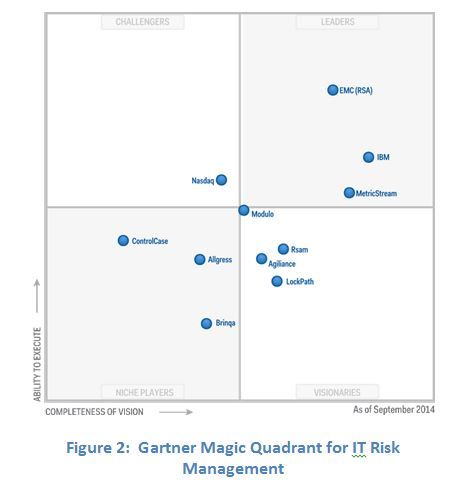
In March, this year, Gartner released their Magic Quadrant for IT Risk Management. Once again, EMC-RSA has been positioned as a Leader!
Some might ask, isn’t IT Vendor Risk Management just a subset of IT Risk Management? Yes, it is but the breadth and complexity of third parties being used in organizations today require the use of risk management solutions like the EMC-RSA Third Party Governance solution that are specifically tailored to the unique requirements associated with third party risk management. These requirements include understanding the complete organizational structure of the third party, the business activities and products and services the third party supports, evaluating the controls that the third party has in place to mitigate risk, what type of risk transfer the third party has in place, and establishing and monitoring performance indicators unique to the products and services being delivered by the third party. These requirements are unique enough that they cannot be adequately addressed by broader IT Risk Management solutions.
Broader IT Risk Management solutions tend to be more inwardly focused, placing attention on the organization’s internal processes and internal control framework to manage risk. Compliance with information security regulations such as the Gramm-Leach Bliley Act (GLBA) highlight the necessity of both solutions. On the one hand, you must understand the population of vendors your organization is using, which of the organization’s products and services they support, how they support them, what kinds and amounts of information are being shared, and the control procedures the third party has in place to protect the information being shared and to ensure the third party’s resiliency. The target of understanding in all cases is the third party and the specific products and services they are delivering.
There is, however, a broader aspect to GLBA that targets the organization’s internal processes, policies and procedures, and internal controls. These include documenting non-third party related threat sources that may compromise information security – such as employee accidental loss or deliberate theft of customer information, and data breaches that might occur as a result of compromised application systems and network devices. Internal controls around information security must also be documented such as how new employees are vetted and on-boarded, how existing employees receive effective on-going training on information security, and how and when security patches are applied to IT assets. The organization’s policies and procedures to manage information security and GLBA compliance must be documented and associated with the actual regulation in order to demonstrate to executive management and regulators how the organization achieves compliance. Lastly, information security incidents that occur must be managed in a timely manner to minimize the duration and impact of the incident and to make certain all regulatory reporting requirements are fulfilled.
These two RSA Archer solutions can help you obtain the most comprehensive understanding and management of IT-related risk, whether it originates internally or through third parties!
For more information on these Gartner assessments, please visit this landing page.
These graphics were published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner documents are available upon request from EMC-RSA. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation.
Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
- Gartner Report: For CIOs: Environmental, Sustainability, Governance, and IT Risk Management in the Digital Age in CRO Pathway Blogs
- Streamline Compliance for NERC with Karta Management App-Pack in Archer Blogs
- Archer Exchange announces NERC, ESG, and Third-Party Offerings for February 2024 in Archer Blogs
- Shine Brighter Than Ever Before! in Archer Blogs
- Empowering Institutional Investors with Innovative ESG Portfolio Management Solution in Archer Blogs