Important Update: Community URLs redirect issues are partially resolved. Learn More. .
- Archer Community
- News, Events & Groups
- Archer Blogs
- The Operational Risk Management Journey (part II)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In part I of this blog, I described the typical maturity progression of an Operational Risk Management Program.
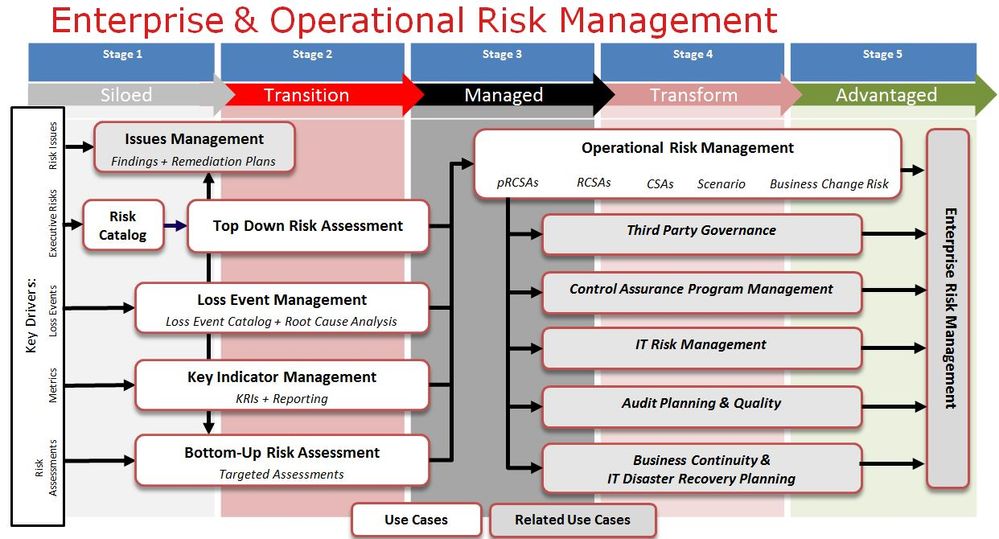
Recognizing the fact that risk management programs go through multiple stages of maturity, maturing over time, with RSA Archer 6.1, we have aligned our solution use cases with the maturity journey. In this way, customers are acquiring just the right amount of technology to enable their Operational Risk Management program as they need it. They are not biting off more than they can chew or over purchasing functionality they may never use.
RSA Archer 6.1 enables organizations to better take command of their GRC Journey, empowering organizations to incrementally build their Operational Risk Management program as it matures. The Operational Risk Management-related activities (or use cases) we typically see implemented as organizations build their risk management program are as follows:
Issues Management is a core foundational use case to document and manage audit issues and issues identified by management and external parties. It captures issues that may arise through the implementation of other use cases. From this foundation, the following use cases are often enabled. The exact sequence of the following use cases depends on your business priorities and resources.
Risk Catalog is also a foundational use case for organizations that only want a central location to document their risks, typically moving from an EXCEL or Sharepoint based approach. With Risk Catalog you get a place to document your organization’s risk and roll granular risk statements up to intermediate and enterprise risk statements. You also get basic qualitative risk assessment. You do not get several element of a more robust risk register that provide greater business context through association with business processes, internal controls, and other risk treatment.
Top-Down Risk Assessment gives you the capability to catalog and associate your business processes, risks, and controls to better understand business activities and the internal control framework. You can assess the inherent and residual risk of each risk register record using qualitative and monetary values across multiple risk categories. Furthermore, risk register records can be aggregated and rolled up to intermediate and enterprise risk statements and reporting allows you the capability to drill through records to understand the business context and drivers of risk
Loss Event Management gives you a means to capture internal losses, near misses, and relevant external loss events, perform root cause analysis, execute workflow to communicate, analyze, and approve losses, calibrate external loss events, and produce numerous relevant loss reports
Key Indicator Management allows you to document key risk, control, performance, and business indicators. Indicator values can be collected from source systems or via manual input from data owners. In any case, you can oversee that all data is collected in a timely manner and that missing data and indicators outside acceptable limits are communicated and addressed in an appropriate and timely manner.
Bottom-Up Risk Assessment allows you the capability to perform consistent risk assessments on projects and activities such as new and changing business processes, products and services, M&As, and fraud incidents. Questionnaires can be created and repeatedly used to ensure all items in scope are being considered consistently.
The Operational Risk Management use case pulls all of these other use cases together to enable greater business context and introduces a purpose built solution to initiate and manage self-assessments. Three different kinds of assessments can be automatically created (Control self-assessments (CSAs), Risk and Control self-assessments (RCSAs), and Process, Risk, and Control Assessments (pRCSAs)) and distributed to the first line of defense (business unit managers), for completion through the use of an intuitive interface. The overall status of the assessment campaign can be monitored by the second line of defense and when assessments are completed, they are routed to the designated second line of defense persons to review, challenge, and reroute, if needed. At the completion of the assessment campaign, when all assessments have been approved by the 2ND line of defense, the results are automatically updated to the risk and control registers. Lastly, the Operational Risk Management use case provides a means to document and manage your organizations insurance program and understand which risks are being transferred and whether the coverage is adequate.
By integrating Adjacent use cases available from RSA Archer you can create an Enterprise view of risk
We realize that risk management is not a challenge that can be solved simply with technology. It is a business imperative that must be addressed through a shift in focus, priority and culture within your organization, making risk management part of how everyone in your organization thinks and acts. By engaging everyone in the risk process, you can eliminate operational inefficiency and achieve your most strategic growth objectives. That’s why our collective mission at RSA Archer is to “Inspire Everyone to Own Risk.” That is our passion. That is our commitment.
- Announcing Archer RMIS AI! in Archer Blogs
- Automating ESG Compliance with Archer in Archer Blogs
- Archer ESG Management: Keeping Pace with the Latest SASB Standards Updates in Archer Blogs
- Use Archer NIST-Aligned AI Risk Management Framework to Secure the Future of Artificial Intelligence in Archer Blogs
- An Elevated Archer Exchange User Experience is now Available! in Archer Blogs