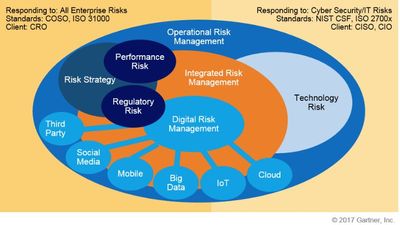
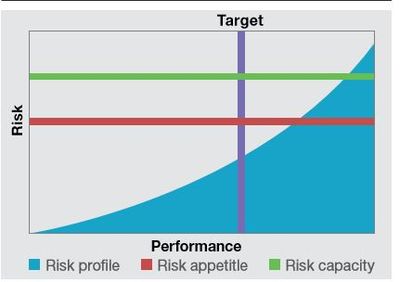
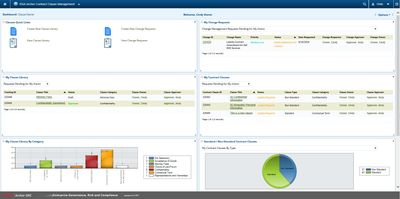
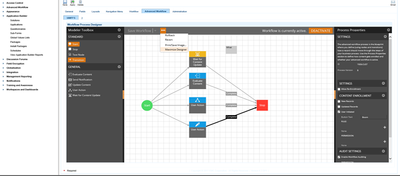
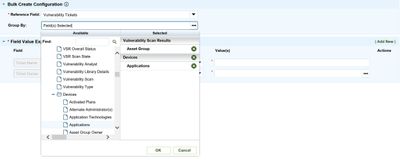
RSA Archer PCI Management
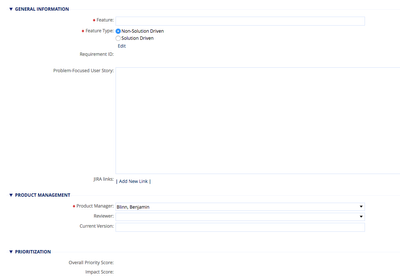
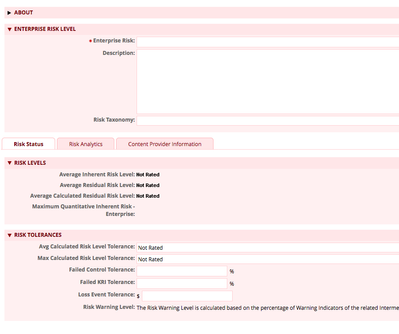
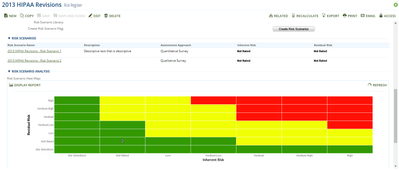
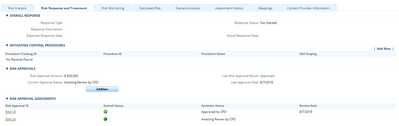
What are the basics of PCI-DSS Compliance?The Payment Card Industry Data Security Standard (PCI-DSS) defines a consolidated set of security best practices endorsed by major card brands, which are designed to reduce fraud risk associated with credit c...