In my previous blog, New Job Chapter One, I described an approach using RSA Archer to drive your Business-Driven Security strategy. I want to emphasize a couple of points critical to an organization demonstrating their compliance with information security-related regulations like the EU-GDPR, GLBA, NY State Cybersecurity laws, etc. Here, again, is the BizDS flowchart I introduced:
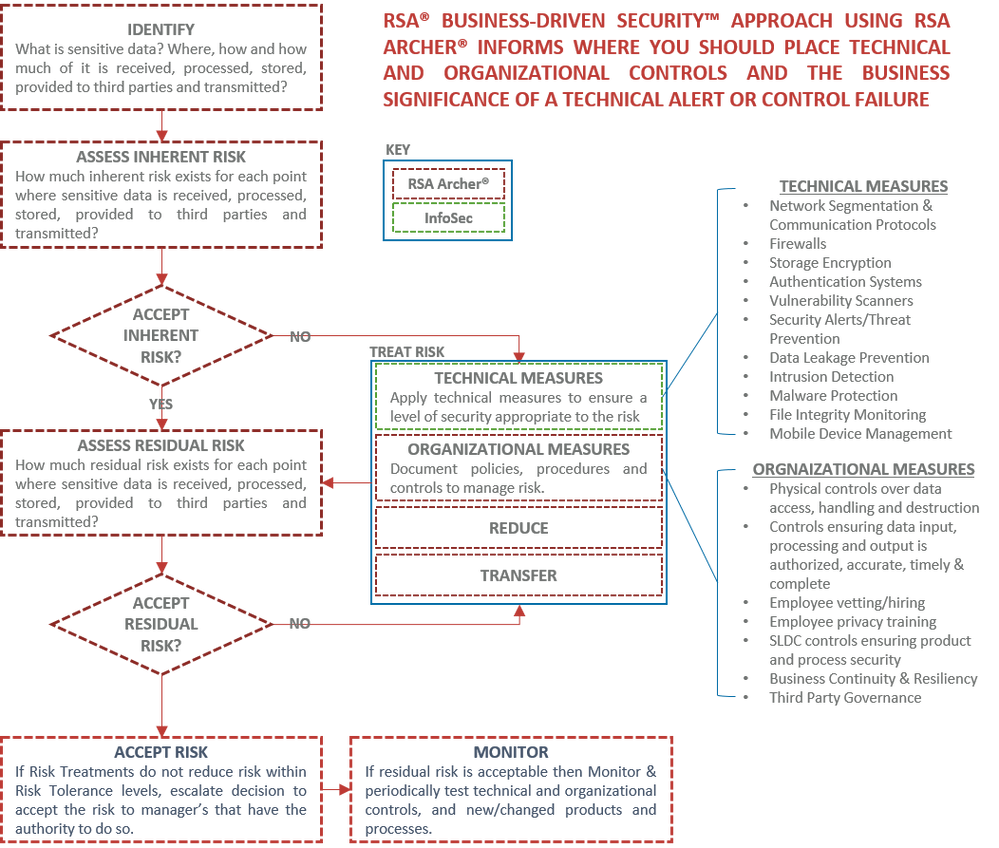
RSA Archer is used to capture the products and services, IT infrastructure and business processes of the organization (Applications, Servers, Databases, Data stores, devices, web-facing services, etc.). The type, format (physical or electronic), criticality, and the amount of information handled by or through each business process and each piece of IT infrastructure is documented and the inherent risk of each is calculated. You now have the information necessary to make decisions about where to apply technical controls (Identity, SEIM, Vulnerability scanners, Firewalls, etc.) and organizational controls (physical access, employee background checks, codes of conduct, SDLC management, training, third-party controls, resiliency, etc.).
As you move into the monitoring phase of your information security program, technical controls and organizational control indicators are generating a tidal wave of data, suggesting that there may be weaknesses in your protection of information. Utilizing a Business Driven Security strategy, the data thrown off by technical controls and organizational control metrics is married back up with the information you have already evaluated about your business processes and IT infrastructure using Archer. By combining this information you are able to effectively wade through the sea of technical information, understand its business context in terms that are meaningful to the business, prioritizing your response to the information based on its significance to your organization and the resources you have available to work the problems. Sometimes you are overwhelmed with the number and significance of security gaps and issues to address. A Business Driven Security strategy helps your technical teams to articulate these gaps and issues in a form the business understands so that they can make meaningful decisions regarding the allocation of additional capital and human resource investments to remedy the problems.
In summary, for an organization trying to demonstrate it's compliance with information security-related regulations like the EU-GDPR, GLBA, NY privacy law, etc., it is essential to demonstrate you can answer these questions:
- Does the organization know what, where, and how much regulated information is managed by the organization and how much risk it poses?
- Have the technical and organizational risk treatments been implemented around those points where high-risk information is processed, handled, stored, or transmitted in some manner?
- Are the technical and organizational controls operating effectively and are the events, vulnerabilities, warnings and exceptions generated being addressed in accordance with the business risk they represent?
A mature business-driven security strategy answers these questions and can help an organization demonstrate compliance with their regulatory obligations around information security.
We explore how to implement a Business Driven Security strategy in more detail in this white paper
