Important Update: Community URLs redirect issues are partially resolved. Learn More. .
- Archer Community
- News, Events & Groups
- Archer Blogs
- 2 Steps for Managing RSA Archer Support Requests
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Congratulations, your use case is live! You have successfully automated your business process with RSA Archer. After a team high-five and a few moments of contemplation of your team’s shear awesomeness, you hear the “ding” of your email inbox wind up like a month-long holiday radio station. Upon reviewing said inbox, you note a growing list of requests asking:
- Would you grant access to this great new business process for my whole team?
- Can I request a data import to speed up the data entry process?
- I love this report…but could we tweak it to add X value?
- Can we add another status option to field Y?
- Can we use RSA Archer to manage Z risks? How about our Friday donut club?
- Oops! I accidentally added this record. Could you delete it for me?
In the RSA Archer world, a successful risk and compliance program can feel like you’ve climbed the highest peak. And past the peak, that success can overwhelm your team post-implementation with a snowball of requests for enhancements, access requests, and more. Complicating matters, these requests are usually emailed to the GRC team or business process owner and often lack the necessary details needed to adequately define the request’s requirements. Large volumes of these type of requests can overwhelm business process owners and Archer admins who are typically responsible for reviewing the requests, evaluating their impact to the existing business process, and determining their priority to the business. Organizations must establish a governance process to manage and prioritize these requests as their volume increases.
At RSA Charge in October, one of our amazing presenters provided an all too familiar example highlighting the need for a change request program. As their team prepared a business process demonstration for the on-site bank examiners, they noticed a field in their application records suddenly appeared blank. After careful review, it was determined that another team using this “shared” application in RSA Archer decided they weren’t using that particular field…and deleted it.
Unfortunately, this is not an uncommon scenario. But there are two steps that your organization can take to minimize the potential this scenario will happen to you.
Step 1: Institute an RSA Archer Control Board
Business processes require oversight and governance; so does the technology that automates and manages those business processes. A Control Board can ensure that any enhancements or changes to the business process complement or enhance the current risk management process within your organization. An RSA Archer Control Board is responsible for your organization’s RSA Archer roadmap and can review short term minor changes as well as plan for larger projects in the future that may involve more staffing and investment.
The Control Board reviews proposed requests and evaluates the impact the requested change may have to other business processes, applications, questionnaires, calculations, reports, iViews, workspaces, and more. In addition, this team can prioritize the requests based on business need, impact, legal review, effort, and more.
Fortunately, there are many mountain climbers that have forged a successful path ahead and can offer guidance on setting up Archer Control Boards. In fact, several presenters provided their best practices and lessons learned at RSA Charge 2017 and their presentations are available (here and here) on the RSA Archer community. (Please note, these links require access to the RSA Archer Customer/Partner Community.)
Step 2: Automate Your Support Request Process
Managing change requests for your RSA Archer implementation is simply a governance business process. So, why not automate it?
The good news: RSA Archer has done all of the hard work for you! On November 14, we released the RSA Archer Support Request app-pack to capture end user requests for enhancing RSA Archer business processes. Organizations can easily manage their business teams’ ideas including:
- Business process improvements, innovations, or changes;
- Suggestions for new reports or changes to existing reports;
- Requests to delete records;
- Proposals for updating dashboards and iViews;
- Enhancements application layouts;
- User access requests, and more.
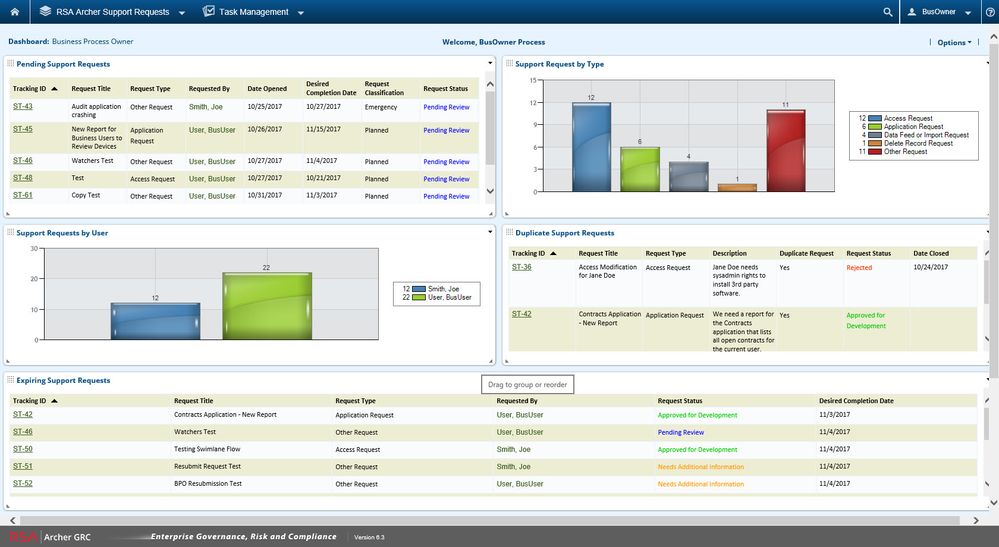
In addition, the RSA Archer Support Requests app-pack assists business process owners in defining enhancement requirements, level of effort, and prioritizing incoming requests. Once the request has been approved, the RSA Archer Administrator can manage the development status and document progress as the request is being developed and deployed.
With RSA Archer Support Requests, your Control Board can track, prioritize, and implement requested changes to your RSA Archer implementation allowing your organization to quickly respond to business requests and minimizes disruption to the system and existing business processes.
Interested in learning more about the RSA Archer Support Requests app-pack? Join us for a Free Friday Tech Huddle on December 1, 2017. In addition, a demonstration video is available on the RSA Exchange. Check it out and let us know what you think!
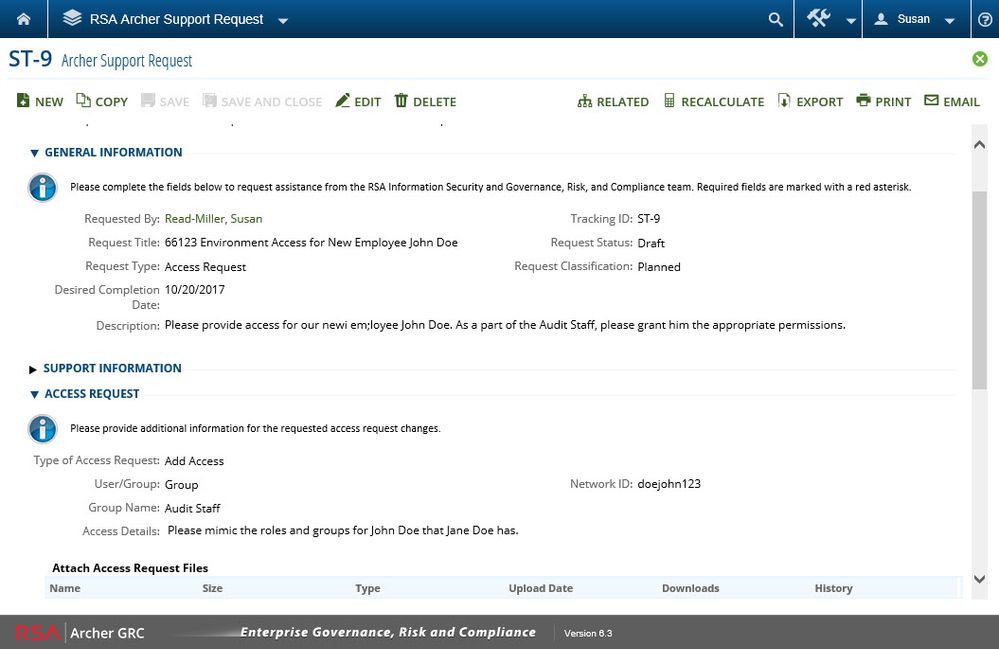
RSA Archer Support Request for Access
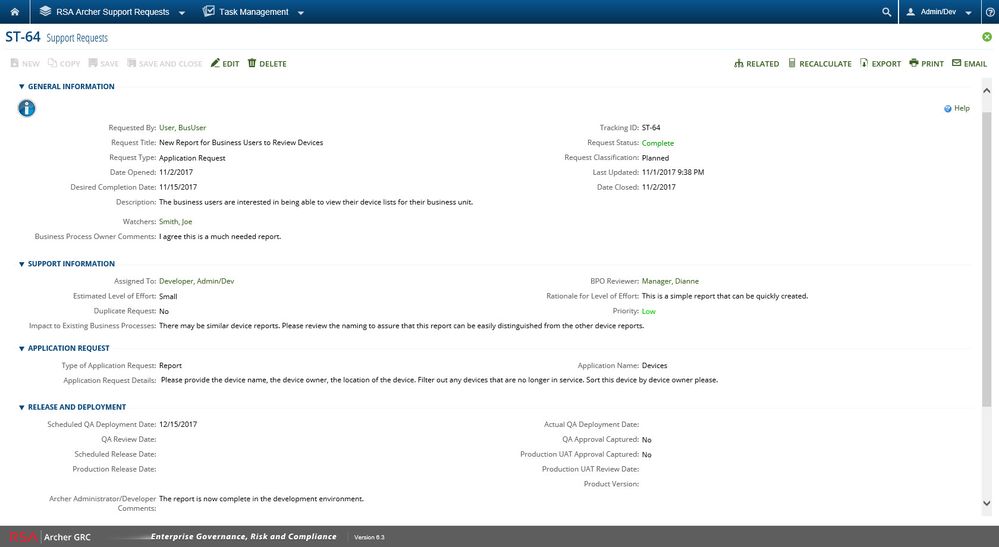
Completed Request for a Report Enhancement
- Engage 4.2.0: Understanding Requester access to published records on Engage portal in Archer Blogs
- Multi-Lingual support in Engage in Archer Blogs
- Maintaining Compliance with Conflicts of Interest, Gift, and Hospitality Policies in Archer Blogs
- Understanding Your Stakeholders with Archer Complaints Tracking in Archer Blogs
- How to use Engage for Vendors with new UI for Assessment and Home Page in Archer Blogs